Elliptic Curves in Cryptography: Unlocking the Secrets with London Mathematical Society Lecture Note 265

In the realm of cryptography, elliptic curves have emerged as a transformative technique, offering unparalleled security and efficiency. This article delves into the captivating world of elliptic curves in cryptography, exploring the fundamental concepts and showcasing the groundbreaking work presented in London Mathematical Society Lecture Note 265.
The Essence of Elliptic Curves
Elliptic curves are mathematical objects defined by an equation of the form y² = x³ + ax + b. They possess unique properties that make them particularly well-suited for cryptographic applications. Unlike traditional cryptographic techniques that rely on large numbers, elliptic curves utilize the geometric properties of these curves to achieve robust security.
Applications in Cryptography
Elliptic curves have revolutionized cryptography in numerous ways, including:
- Encryption and Decryption: Elliptic curve cryptography (ECC) provides robust encryption and decryption algorithms, ensuring secure communication and data transmission.
- Digital Signatures: ECC enables the creation of digital signatures, allowing users to authenticate messages and verify their integrity.
- Key Exchange: Elliptic curves facilitate secure key exchange, establishing shared secret keys between communicating parties.
London Mathematical Society Lecture Note 265: A Comprehensive Guide
London Mathematical Society Lecture Note 265, authored by Neil Koblitz, is a seminal work that provides a comprehensive to elliptic curves in cryptography. This invaluable resource covers:
- Mathematical Foundations: A thorough exploration of the mathematical underpinnings of elliptic curves, including their algebraic and geometric properties.
- Cryptographic Applications: An in-depth examination of how elliptic curves are used in various cryptographic techniques, such as encryption, digital signatures, and key exchange.
- Implementation Considerations: Practical advice on implementing elliptic curve cryptography in real-world systems, addressing issues of efficiency and security.

Advantages of Elliptic Curve Cryptography
ECC offers numerous advantages over traditional cryptographic techniques, including:
- Enhanced Security: ECC provides a higher level of security compared to RSA and other traditional methods.
- Efficiency: Elliptic curve algorithms require shorter keys and smaller computations, resulting in improved performance.
- Compactness: ECC key pairs and signatures are significantly smaller in size.
- Quantum Resistance: Elliptic curves are believed to be resistant to quantum computing attacks.
Applications in the Real World
Elliptic curves in cryptography have found widespread applications in:
- Blockchain and Cryptocurrency: ECC is used in Bitcoin, Ethereum, and other cryptocurrencies to secure transactions and protect user privacy.
- Digital Certificates: ECC-based digital certificates are employed to authenticate websites and secure online communication.
- Smart Cards: ECC is used in smart cards to provide secure access to financial and other sensitive data.
Elliptic curves in cryptography have revolutionized the field of information security. London Mathematical Society Lecture Note 265 serves as an indispensable guide to this captivating technique, providing a comprehensive understanding of its mathematical foundations, cryptographic applications, and real-world implementations. By unlocking the secrets of elliptic curves, you can harness the power of this advanced cryptography to protect your data, secure your communications, and navigate the digital landscape with confidence.
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Alexis Stephens
Alexis Stephens Libby Hinsley
Libby Hinsley Shikhar Anand
Shikhar Anand Robert F Burgess
Robert F Burgess Malcolm Mccullough
Malcolm Mccullough Lucio Giuliodori
Lucio Giuliodori Lesley Crossingham
Lesley Crossingham Erica Sirotich
Erica Sirotich Frank Ryan
Frank Ryan John Fabian
John Fabian Leon Gunther
Leon Gunther Paul Holtham
Paul Holtham Emily R King
Emily R King Zulebia Esmail
Zulebia Esmail Rebecca Wescott
Rebecca Wescott Galina Krasskova
Galina Krasskova Aaron B O Connell
Aaron B O Connell Riley Hart
Riley Hart Arie M Winograd
Arie M Winograd Anni Gethin
Anni Gethin
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Zachary CoxLost Circulation And Wellbore Strengthening: The Ultimate Guide for Drilling...
Zachary CoxLost Circulation And Wellbore Strengthening: The Ultimate Guide for Drilling...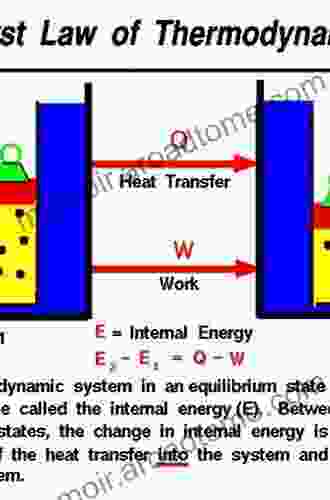
 Jonathan HayesPrinciples of Thermodynamics: A Comprehensive Guide to the Fundamental Laws...
Jonathan HayesPrinciples of Thermodynamics: A Comprehensive Guide to the Fundamental Laws... Vladimir NabokovFollow ·15.9k
Vladimir NabokovFollow ·15.9k Lucas ReedFollow ·19.4k
Lucas ReedFollow ·19.4k Colton CarterFollow ·16.8k
Colton CarterFollow ·16.8k Jared NelsonFollow ·3k
Jared NelsonFollow ·3k Isaiah PowellFollow ·15.6k
Isaiah PowellFollow ·15.6k Blake BellFollow ·6.9k
Blake BellFollow ·6.9k Tennessee WilliamsFollow ·2.9k
Tennessee WilliamsFollow ·2.9k Jett PowellFollow ·11.9k
Jett PowellFollow ·11.9k

 Henry Green
Henry GreenCorrosion and Its Consequences for Reinforced Concrete...
Corrosion is a major threat to reinforced...

 James Gray
James GrayDiscover the Enigmatic World of Pascin in "Pascin Mega...
Immerse Yourself in the...

 George R.R. Martin
George R.R. MartinUnlocking the Power of Nature: Delve into the Bioactive...
In a world increasingly...

 Julian Powell
Julian PowellMaster the Art of Apple Watch App Development: A...
Unlock the Potential of Apple Watch Apps In...
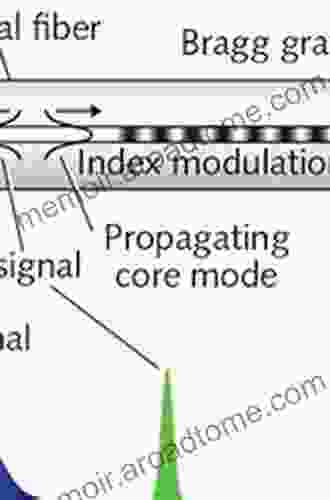
 Jaylen Mitchell
Jaylen MitchellPlastic Optical Fiber Sensors: A Comprehensive Guide to...
In the rapidly evolving landscape of...

 Truman Capote
Truman CapoteUnlock the Secrets of Language Creation: Dive into...
The realm of computer science...