Managing Proliferation of Confidential Data on Corporate and BYOD Devices: A Comprehensive Guide

In the modern digital landscape, confidential data has become a double-edged sword. While it empowers businesses and individuals with valuable insights and operational efficiency, its uncontrolled proliferation poses significant security risks.
5 out of 5
| Language | : | English |
| File size | : | 2587 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 205 pages |
The proliferation of confidential data is particularly acute on corporate and Bring Your Own Device (BYOD) devices. Employees often store and access sensitive data on a myriad of devices, creating a fragmented and vulnerable data landscape.
Challenges of Confidential Data Proliferation
- Increased risk of data breaches: The more devices that access confidential data, the greater the number of potential entry points for malicious actors.
- Compliance violations: Uncontrolled data proliferation can lead to non-compliance with industry regulations and privacy laws, exposing organizations to fines and reputational damage.
- Operational inefficiencies: Managing and securing confidential data across multiple devices can strain IT resources and hinder productivity.
Effective Strategies for Managing Data Proliferation
To mitigate the risks posed by confidential data proliferation, organizations must implement a comprehensive data protection strategy that encompasses the following elements:
1. Data Discovery and Classification
The first step towards effective data protection is identifying and classifying all confidential data within the organization. This involves conducting a thorough data audit to map out where data is stored and who has access to it.
2. Data Access Control
Once confidential data has been identified, organizations must implement robust access controls to restrict who can view, edit, or delete the data. This includes using strong authentication methods, such as two-factor authentication, and implementing role-based access controls.
3. Data Encryption
Encryption is essential for protecting confidential data at rest and in transit. By encrypting data, organizations can render it unreadable to unauthorized individuals, even if they gain access to it.
4. Data Loss Prevention (DLP)
DLP solutions monitor and control the transfer of confidential data across devices and networks. They can prevent sensitive data from being shared with unauthorized parties or transferred to insecure locations.
5. Data Governance
A well-defined data governance framework ensures that confidential data is managed and protected in a consistent and compliant manner across the organization. This framework should include policies and procedures for data storage, access, and disposal.
Benefits of Implementing a Robust Data Protection Solution
Implementing a comprehensive data protection solution provides numerous benefits for organizations, including:
- Reduced risk of data breaches: By implementing strong security measures, organizations can significantly reduce the likelihood of confidential data breaches.
- Improved compliance: A robust data protection solution helps organizations comply with industry regulations and privacy laws, avoiding fines and reputational damage.
- Increased operational efficiency: By centralizing and automating data protection processes, organizations can streamline IT operations and improve productivity.
- Enhanced data privacy: A data protection solution protects the privacy of employees and customers by ensuring that their confidential data is handled securely and ethically.
The uncontrolled proliferation of confidential data on corporate and BYOD devices poses significant security risks for organizations. To mitigate these risks, organizations must implement a comprehensive data protection strategy that includes data discovery and classification, data access control, data encryption, data loss prevention, and data governance. By implementing a robust data protection solution, organizations can reduce the risk of data breaches, improve compliance, increase operational efficiency, and enhance data privacy.
Investing in a data protection solution is an investment in the long-term security and success of your organization. By protecting your confidential data, you protect your reputation, your customers, and your bottom line.
5 out of 5
| Language | : | English |
| File size | : | 2587 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 205 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Michael Hyatt
Michael Hyatt Beverly Carriere Tiner
Beverly Carriere Tiner Charles F Haanel
Charles F Haanel Hunter Vaughan
Hunter Vaughan Sophie Mills
Sophie Mills Trudi Entwistle
Trudi Entwistle Jules Stewart
Jules Stewart M Steven Piver
M Steven Piver Diana Masny
Diana Masny Zeb Kingman
Zeb Kingman Sara Elinoff Acker
Sara Elinoff Acker James R Beck
James R Beck David Bell
David Bell Jeremiah Jefferson
Jeremiah Jefferson Joel T Dudley
Joel T Dudley Meir Schneider
Meir Schneider Mindy Obenhaus
Mindy Obenhaus Jenny Mccarthy
Jenny Mccarthy Lucinda Bassett
Lucinda Bassett Branden Byers
Branden Byers
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Aldous HuxleyDiagnosis Detective: Curing Granulomatous Mastitis: A Comprehensive Guide to...
Aldous HuxleyDiagnosis Detective: Curing Granulomatous Mastitis: A Comprehensive Guide to... Alexander BlairFollow ·12.2k
Alexander BlairFollow ·12.2k Julio CortázarFollow ·2.4k
Julio CortázarFollow ·2.4k Andrew BellFollow ·18k
Andrew BellFollow ·18k Eddie BellFollow ·5.2k
Eddie BellFollow ·5.2k Virginia WoolfFollow ·10.2k
Virginia WoolfFollow ·10.2k Jackson BlairFollow ·16.4k
Jackson BlairFollow ·16.4k Ralph EllisonFollow ·11.8k
Ralph EllisonFollow ·11.8k Nikolai GogolFollow ·7.5k
Nikolai GogolFollow ·7.5k

 Henry Green
Henry GreenCorrosion and Its Consequences for Reinforced Concrete...
Corrosion is a major threat to reinforced...

 James Gray
James GrayDiscover the Enigmatic World of Pascin in "Pascin Mega...
Immerse Yourself in the...

 George R.R. Martin
George R.R. MartinUnlocking the Power of Nature: Delve into the Bioactive...
In a world increasingly...

 Julian Powell
Julian PowellMaster the Art of Apple Watch App Development: A...
Unlock the Potential of Apple Watch Apps In...
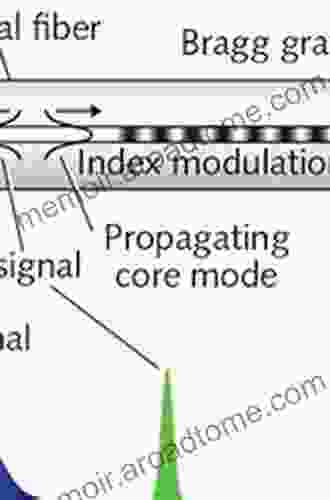
 Jaylen Mitchell
Jaylen MitchellPlastic Optical Fiber Sensors: A Comprehensive Guide to...
In the rapidly evolving landscape of...

 Truman Capote
Truman CapoteUnlock the Secrets of Language Creation: Dive into...
The realm of computer science...
5 out of 5
| Language | : | English |
| File size | : | 2587 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 205 pages |